
Threat Detection and Hunting




Threat Detection and Hunting is a proactive security practice that goes beyond reactive alerting to uncover hidden threats and adversary activity within your environment. By combining threat intelligence, behavioral analytics, and hypothesis-driven investigation, analysts can detect stealthy attacks that evade traditional controls. This approach enables security teams to validate suspicious signals, trace attacker movement across systems, and respond before damage occurs. Effective threat hunting not only improves detection capabilities over time but also strengthens overall security posture by exposing blind spots and informing better defenses.
Identify and prioritize threats based on threat intelligence, risk appetite, industry relevance, and recent attacker activity (e.g., MITRE ATT&CK techniques). This ensures detection efforts align with real-world risks. Gambit Cyber provides a rich feature for Threat Prioritization based on multiple filtering criteria including industry standard GIR Framework.
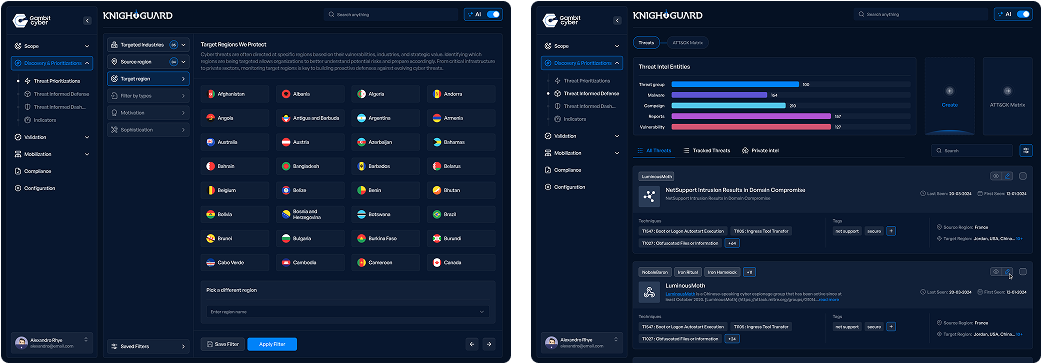
Map out how an attacker would exploit a specific weakness or move through your environment using TTPs. Develop hypotheses for what adversary behavior would look like in logs or telemetry. Use our AI Enabled Threat Scenario generator to quickly generate Threat Scenarios based on your hypothesis.
Translate hypotheses into actionable detection rules. This includes defining log sources, matching patterns, and crafting queries or rules (e.g., Sigma, KQL, Splunk SPL, or YARA). Utilize Ready to deploy detection rules from our extensive repository of Open and Closed Source Intel to quickly operationalise Intel insights. Track and monitor all your Log sources centrally from within the platform to identify which Log sources should be enabled for what TTPs to bring efficiency and consistency to Detection Analytics and reduce SIEM overaload.
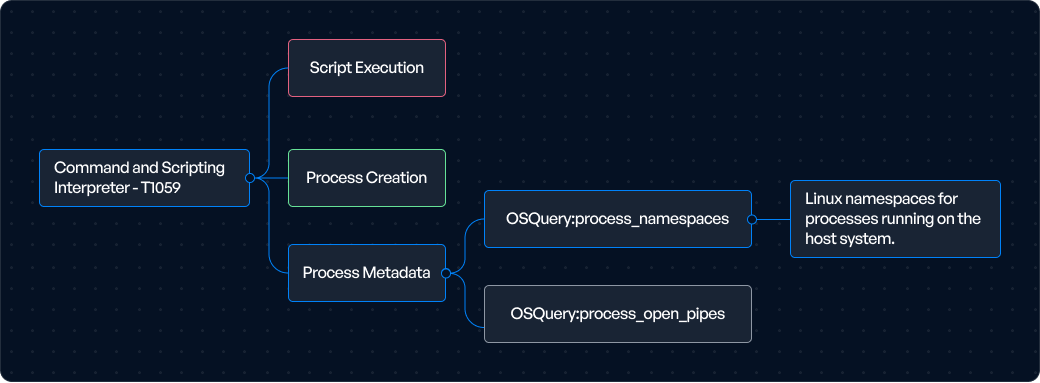
Test detection rules in a controlled environment using simulated attack scenarios (e.g., Atomic Red Team, Scythe, or manual testing). Validate that alerts trigger appropriately and without noise. Seamlessly deploy Detection Analytics to any SIEM of choice and get the logs right in the platform without ever logging into your SIEM saving hours of work for Detection and Hunt Engineers.
Push validated detection logic to production systems (SIEM, EDR, XDR) from within the platform. Schedule emulated Campaigns to detect any shift in Security Controls.

Check out impactful stories and solutions that are shaping cybersecurity outcomes.

Consolidates multiple CTI functions & tools in one single platform to improve productivity and enhance efficiencies. Helps optimize, manage, & measure security operations.
