
Risk and Compliance




Risk and compliance management involves establishing a structured framework of controls to ensure the confidentiality, integrity, and availability of information systems. This includes categorizing assets by impact, assessing and mitigating risks, implementing security safeguards, and continuously monitoring their effectiveness. Organizations must define clear roles and responsibilities, enforce policies for access control, incident response, and system maintenance, and ensure that security practices are aligned with both operational needs and regulatory expectations. Through ongoing assessment and documentation, organizations can demonstrate accountability, reduce exposure to threats, and build trust with stakeholders by maintaining a secure and compliant posture.
Gain insights into your Current Risk Profile and define your Target Risk Profile by systematically visualising your Security Program on Govern, Identify, Protect, Detect, Respond and Recover Functions. Go further deep and understand categories and subcategories relevant to your Risk Profile. Create multiple Risk Profiles based on departemnts, location, GRC compliance framework etc.
Select security controls tailored to your organization's risk profile and compliance obligations. Prioritize controls based on your existing needs and risk apetite. Controls should span technical, administrative, and physical domains and align with industry standards and regulatory requirements.
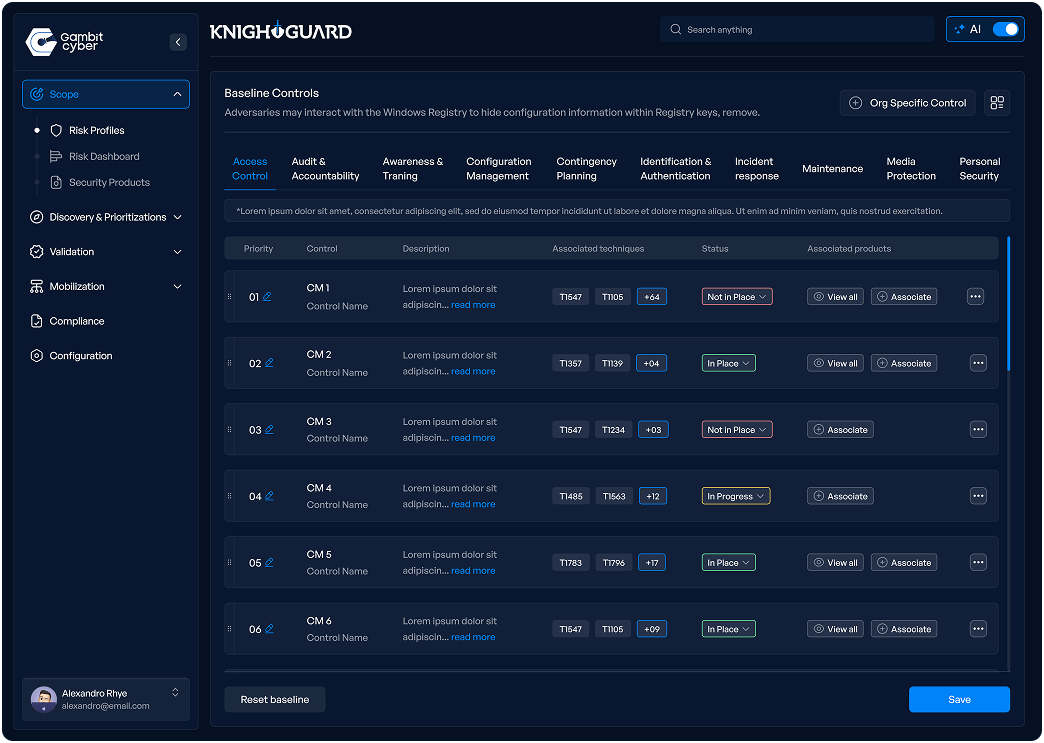
Associate your Security Products with Compliance and Controls definition to gain AI-based Insights and Remediation Playbook on how to implement the policy, procedure or control specific to your environment and save hours in implementation. Gambit Cyber divides each subjective Control into a set of Actionable Tasks that can be tracked like a implementation step making it easier for your team to focus on a single actionable and measurable task. Integrate with any ticketing system of choice our use our inbuilt Ticketing System to track progress.
Track and monitor all Audit and Reporting requirements from a single Consolidate Dashboard and feed it into your overall Effective Security Posture.

Check out impactful stories and solutions that are shaping cybersecurity outcomes.

Consolidates multiple CTI functions & tools in one single platform to improve productivity and enhance efficiencies. Helps optimize, manage, & measure security operations.
