
Adversarial Exposure Validation




Pre-built threat scenarios allow you to rapidly simulate hundreds of likely attack campaigns and exploit paths targeting your organization’s critical assets. This helps uncover security gaps, misconfigurations, and weak controls—enabling more informed threat modeling, faster validation of intelligence, and better alignment with an ever changing adversary behavior.
CTI Analysts find it difficult to unify, identify and prioritize threats across vaiorus Open and Closed Intel sources. Gambit Cyber’s KnightGuard Platform is Threat Intel agnostic, which means, organisations can easily integrate their own Threat Intel feeds and quickly gain a unified insights into the Threat Landscape. Our AI-enabled (fine tuned for a specific organisation) Threat Intel Ingestion pipeline helps organisations quickly convert any Threat Intel Report into actionable Threat Intel in minutes. Once all threats are ingested, quickly filter threats most relevant to you based on our comprehensive and intuitive Threat Filtering. In addition use our integrated single click GIR (General Intel Requirements) filtering to quickly zoom in on threats that matter most.
While identifying and prioritizing threats is important, an equally important piece is monitoring for any behavioural changes in threats (for example: a new Technique is now being used by Black Basta). Threat Monitoring module in Gambit Cyber enables you to be on top of threats. Effective Threat Change Notifications provide per field level changes include old and new values so that you don’t spend time navigating what changed.
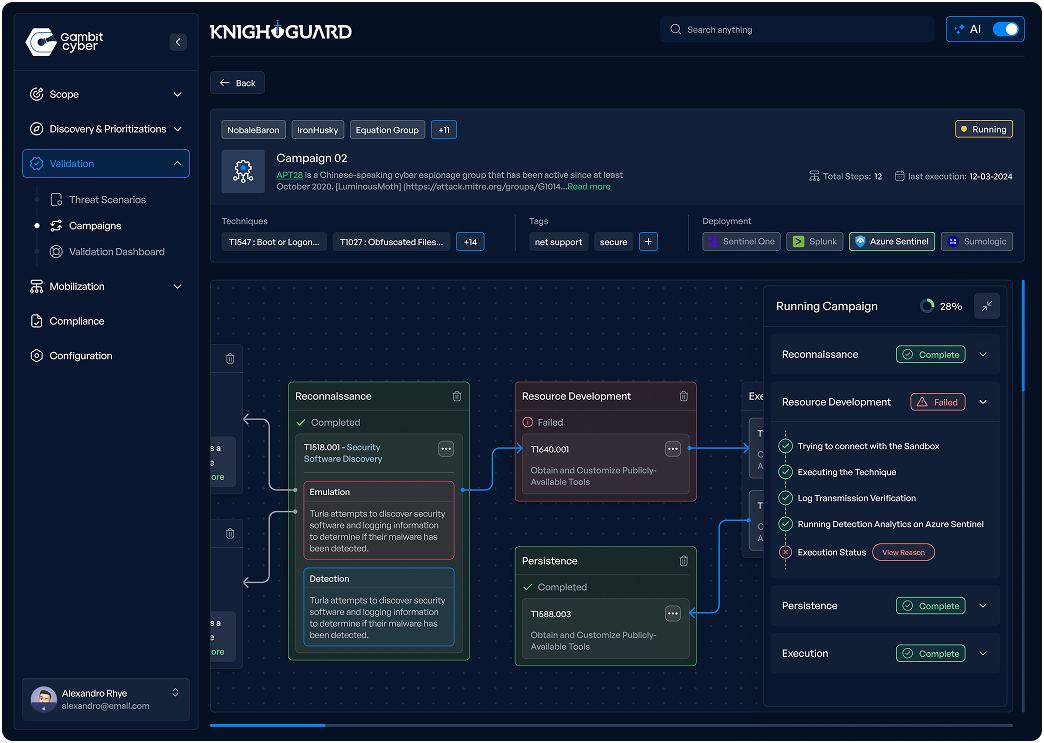
Once the relevant Threats have been identified, quickly generate Emulation Scenarios (aka Campaigns) to enable continous testing against latest Adversary behaviour. Emulation helps reveal how an attacker could chain tactics, techniques, vulnerabilities, weaknesses to reach your critical assets. We provide ready to emulate Threat Scenarios for hundereds of Attack Techniques. Our Red Team AI Agent can help you quickly generate emulation scripts helping you save hours of effort.
Quickly implement, test, validate and deploy Detection Analytics in any language and SIEM format right from the platform to quickly plug any gaps in your Security Controls. Use our Detection Analytics AI Agent to quickly generate Detections in any language format.
With a centralized Dashboard, gain insights into how well your Controls are working against Threats most relevant to your organisations. Map your Detection Analytics on to the MITRE Attack Frameowrk and visualise your Detection gaps and fix them quickly.

Check out impactful stories and solutions that are shaping cybersecurity outcomes.

Consolidates multiple CTI functions & tools in one single platform to improve productivity and enhance efficiencies. Helps optimize, manage, & measure security operations.
